Network protection is an all-encompassing concept and one of the most vital frameworks of any IT infrastructure. Many other IT solutions are often rendered obsolete without a properly secured network. System protection and support services are vital to any business, but if your network protection is not up to standards, you will be constantly putting out one fire after another.
Network security incorporates many different aspects, from access control to firewall protection and basic antivirus protection. Robust network protection does more than help keeps your data and operations secure. It can also reduce labor and expenses by saving time and reducing obstacles in the digital workspace.
Network Firewall
A network firewall is a security device that filters all outgoing and incoming internet traffic on your network. You can think of your firewall as a security guard standing at the entrance to your network. The network firewall filters all incoming or outgoing traffic based on their source or destination. A firewall filters all suspicious or unwanted network traffic. Of course, the firewall allows any safe internet traffic through without issue.
A strong network firewall is important for multiple reasons. First and foremost, it offers network protection. One of the primary functions of any IT solutions package is security from cyber attacks. A properly working firewall defends your network against malware and hackers.
A strong network firewall also keeps your business running efficiently. It’s important to have fast, reliable access to vital data online every day. But your firewall does not just keep unwanted traffic out. It also helps you maintain access to any data you need throughout the workday.
Firewalls can be set up via software or hardware. For MTBW’s network firewall services, we partner with Fortinet to provide comprehensive, industry-leading network security.
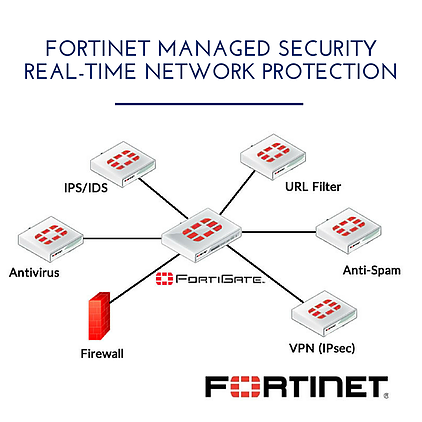
About Fortinet
Fortinet offers a complete range of products and services that work together to provide the most comprehensive, cost-effective, and manageable solutions for protecting networks of all sizes. Fortinet’s award-winning FortiGate™ series of ASIC-accelerated Antivirus Firewalls are the new generation of real-time network protection systems. Specifically, they detect and eliminate the most damaging, content-based threats from email and Web traffic. These can include viruses, worms, intrusions, inappropriate Web content, and more — without degrading performance. In addition to providing application-level protection, the FortiGate systems deliver a full range of network-level services. — firewall, VPN, intrusion detection, and traffic shaping — delivering complete network protection services in dedicated, easily managed platforms.
The FortiGate family proudly spans the full range of network environments and offers cost-effective systems for any application.
All FortiGate Antivirus Firewalls employ Fortinet’s unique FortiASIC™ content processing chip and the powerful, secure, FortiOS™ operating system to achieve breakthrough price/performance. The unique, ASIC-based architecture analyzes content and behavior in real-time, deploying key applications right at the network edge, where they are most effective at protecting enterprise networks.
As the only systems in the world that are certified by the ICSA for antivirus, IPSec, firewall, and intrusion detection functionality, FortiGate systems deliver the highest level of security available. They add a critical layer of real-time, network-based antivirus protection that complements host-based antivirus software and supports “defense-in-depth” strategies without compromising performance or cost. They can be deployed for antivirus protection and content filtering alone in conjunction with the existing firewall, VPN, and related devices, or complete network protection systems with just a simple configuration change.
More About Cyber Security Threats
Of course, being aware of cybersecurity threats can make choosing your network protection a lot easier. Hackers and cyber security threats attack thousands of networks and devices every day. Luckily, knowing what you are up against can make a huge difference.
Malware and Ransomware
Malware is a harmful type of software that can damage or disrupt basic network and system functions. Hackers use unwanted download attachments and malicious files to deliver malware. Hackers also often seek to deliver hardware via fraudulent emails or messages.
On the other hand, Ransomware is a specific type of malware that denies access to a system or certain data until a ransom is paid to the hackers. It is never advised to pay the ransom when you encounter ransomware.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks flood a network with excessive amounts of traffic, users can’t access their system. DDoS attacks are one of the most common types of cyber security attacks. However, DDoS attacks are often accompanied by other cyber security threats. Some will use a DDoS attack as part of a plan to retrieve sensitive data or install malware, for instance.
Phishing
Similar to a DDoS attack, phishing on its own is not usually the end goal. However, phishing is one of the most common forms of cyber security attack. Unfortunately, hackers make phishing emails look authentic by pretending to be an authority figure, such as someone from your organization or government.. Usually, hackers try to extract sensitive information or data from victims through these emails.
Strong network protection and caution are the best things you can do for your organization to protect your cyber security. MTBW offers comprehensive network protection solutions as part of our complete package of IT solutions. Read more about our services to learn about all the ways MTBW can work with your business for perfect IT solutions.





